该板块主要是讲解nmap相关的,刚好前面几个模块以及我测试了几个boxes都需要nmap,但是nmap里具体参数什么作用不是很理解,需要在这个模块搞懂。
Enumeration
Enumeration is the most critical part of all. The aim or goal is not to gain access to our target. Instead, it is identifying all of the ways we could attack a target we must find.
It is not just based on the tools we use. The tools are just tools, they will only do it much faster or more efficiently then human. But tools alone should never replace our knowledge and our attention to detail.
Here it is much more about actively interacting with the individual services to see what information they privide to us and what possibilities they offer to us. It is essential to understand how these tools work and what syntax they use for effective communication and interaction with the different services.
This phase aims to improve our knowledge and understanding of the techniques, protocols, and how they work and learn to deal with new information and adapt to our already acquired knowledge.
Enumeration is collecting as much information as possible. The more information we have, the easier it will be for us to find vectors to attack. It's not too hard to get access to the target system once we know how to do it. Most of the ways we can get access we can narrow down to the following two points:
Functions and/or resources that allow us to interact with the target and/or provide addtional information
Information that provides us with even more important information to access our target.
When scanning and inspecting, we look exactly for these two possibilities. Most of information we get comes from themisconfigurations or neglect of security for the respective services. By the way, misconfiguration are either the result of ignorance or a wrong security mindset. So, only relying on the firewall, Group Policy Objects, and continuous updates is not enough to secure the network.
So, Manual enumeration is a critical component. Many scanning tools simplify and accelerate the process. So, they may miss important information such as service/port if the target does not response to the scanning as some configuration. For example, scanning tools may have a timeout set until they receive a response from the service. So, we have to understand how the enumeration runs.
Introduction to Nmap
Nmap or Network mapper is an open-source network analysis and security auditing tool. It can be used to identify services, applications, hosts, operating systems and versions. Besides, it also offers scanning capabilities that can determine if packet filters, firewalls, or IDS(intrusion detection systems) are configured as needed.
Use Cases
Audit the security aspects of networks
Simulate penetration tests
Check firewall and IDS settings and configurations
Types of possible connections
Network mapping
Response analysis
Identify open ports
Vulnerability assessment as well.
Nmap Architecture
Nmap offers many different types of scans that can be used to obtain various results about the targets.
Host discovery
Port scanning
Service enumeration and detection
OS detection
Scriptable interaction with the target service (Nmap Scripting Engine)
Syntax
chaostudy@htb[/htb]$ nmap <scan types> <options> <target>In help documents, we can find there are lots of scanning techniques
┌─[✗]─[chao@parrot]─[~/Desktop]
└──╼ $nmap --help
Nmap 7.94SVN ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER:
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
--exclude-ports <port ranges>: Exclude the specified ports from scanning
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports sequentially - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma-separated list of script-files or
script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take <time> are in seconds, or append 'ms' (milliseconds),
's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING:
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies
--data <hex string>: Append a custom payload to sent packets
--data-string <string>: Append a custom ASCII string to sent packets
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT:
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--noninteractive: Disable runtime interactions via keyboard
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC:
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
┌─[chao@parrot]─[~/Desktop]
└──╼ $Scan Techniques
For exmaple, scanning techniques offers:
chaostudy@htb[/htb]$ nmap --help
<SNIP>
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
<SNIP>The -sS or TCP-SYN scan is one of the default settings. This scan method makes it possible to scan thousand ports per second. The TCP-TYN scan use three-way handshake to identicy different status of target's port.
Open: If our target sends an SYN-ACK packet back to the scanned port, Nmap detect that the port is open.
Closed: If receives an RST flag, it is an indicator that the port is closed.
Filtered: If Nmap does not receive any of packet back, it will display it as filtered as there are firewall on the target machine may drop or ignore some packets.
For example,
In this example, we can see that we have four different TCP ports open. In the first column, we see the number of the port. Then, in the second column, we see the service's status and then what kind of service it is.
chaostudy@htb[/htb]$ sudo nmap -sS localhost
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-11 22:50 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000010s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5432/tcp open postgresql
5901/tcp open vnc-1
Nmap done: 1 IP address (1 host up) scanned in 0.18 secondsHost Discovery
When we need to conduct an internal penetration test for the entire network of a organization or company,then we should, first of all, get an overview of which systems are online that we can work with. To actively discover such system on the network, we can use variousNmap discovery options. The most effective host discovery method is to use ping or ICMP echo requests.
[!NOTE]
It is always recommanded to store every single scan. This can later be used for comparison, documentation, and reporting. After all, different tools may produce differernt results. Therefore it can be beneficial to distinguish which tool produces which results.
Scan Network Range
nmap + ip range can achieve what we need, but we need more option to speed and narrow the results,
sudo nmap 10.129.2.0/24 -sn -oA tnet | grep for | cut -d" " -f5
10.129.2.32
10.129.2.47
10.129.2.49
10.129.2.80
10.129.2.219nmap 10.129.2.0/24 scans 10.129.2.0 range
-sn Only does Ping scan to identify which machine is alive, disable port scan
-oA tnet outputs results to tnet file in three format (normal, XML, and grepable)
| grep for from the results to grep, and filter all lines that contain "for"
| cut -d" " -f5 from the results to cut, use space or " " as divider and take out the fifth field from each line
By the way, this method works only if the firewall allow it. Otherwise, we have to use other scanning techniques.
Scan IP list
It is not uncommon that user may provide us an IP list with the hosts we need to test. Nmap also gives use the option of working with lists and reading the hosts from this list instead of manually defining.
For exmaple, hosts.lst is a file contains some predefined list.
┌─[chao@parrot]─[~/Desktop]
└──╼ $cat hosts.lst
10.129.2.4
10.129.2.8
10.129.2.12
10.129.2.24
10.129.2.32
10.129.2.47
10.129.2.49
10.129.2.80
10.129.2.144
10.129.2.219Then, use nmap to scan this list file,
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap -sn -oA tnet -iL hosts.lst | grep for | cut -d" " -f5
10.129.2.32
10.129.2.47
10.129.2.49
10.129.2.80
10.129.2.219-iL hosts.lst reads the list of target hosts from the hosts.lst file or performs defined scans against targets in provided 'hosts.lst' list
In this example, some of hosts ignore the default ICMP echo requests as their firewall configuration or they are not alive. Nmap marks them as inactive.
Scan Multiple IPs
An alternated method in Nmap allow use to scan a small part of a network such as specify multiple IP addresses.
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap -sn -oA tnet 10.129.2.46 10.129.2.47 10.129.2.48 10.129.2.49 | grep for | cut -d" " -f5
10.129.2.47
10.129.2.49If these IP address are next to each other, we can also define the range in the respective octet.
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap -sn -oA tnet 10.129.2.46-49 | grep for | cut -d" " -f5
10.129.2.47
10.129.2.49Scan Single IP
For the single host open ports and service scan, we first to determine if it is alive ornot.
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap -sn -oA host 10.129.2.47
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-16 12:47 NZST
Nmap scan report for 10.129.2.47
Host is up (0.59s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.65 secondsGenerally, if we use -sn or disable port scan, Nmap will automatically ping scan with ICMP Echo Requests or -PE. But, before the Ping request, the first packet sent from Nmap is ARP packet.
chaostudy@htb[/htb]$ sudo nmap 10.129.2.18 -sn -oA host -PE --packet-trace
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-15 00:08 CEST
SENT (0.0074s) ARP who-has 10.129.2.18 tell 10.10.14.2
RCVD (0.0309s) ARP reply 10.129.2.18 is-at DE:AD:00:00:BE:EF
Nmap scan report for 10.129.2.18
Host is up (0.023s latency).
MAC Address: DE:AD:00:00:BE:EF
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds-PE perform the ping scan by using ICMP Echo requests against the target
--packet-trace Shows all packet sent and received
[!NOTE]
You can see the ARP packet only at the first scan, then your machine will store the mac table.
Another way to determine why Nmap mark our target as alive is using --reason
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap -sn 10.129.2.47 -PE --reason
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-16 13:03 NZST
Nmap scan report for 10.129.2.47
Host is up, received echo-reply ttl 63 (0.34s latency).
Nmap done: 1 IP address (1 host up) scanned in 5.96 seconds--reason show the reason why the target is alive or not
If we do not need arp packet, we can turn it off
chaostudy@htb[/htb]$ sudo nmap 10.129.2.18 -sn -oA host -PE --packet-trace --disable-arp-ping
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-15 00:12 CEST
SENT (0.0107s) ICMP [10.10.14.2 > 10.129.2.18 Echo request (type=8/code=0) id=13607 seq=0] IP [ttl=255 id=23541 iplen=28 ]
RCVD (0.0152s) ICMP [10.129.2.18 > 10.10.14.2 Echo reply (type=0/code=0) id=13607 seq=0] IP [ttl=128 id=40622 iplen=28 ]
Nmap scan report for 10.129.2.18
Host is up (0.086s latency).
MAC Address: DE:AD:00:00:BE:EF
Nmap done: 1 IP address (1 host up) scanned in 0.11 secondsHere is the offical documentation, Nmap host discovery.
Host and Port Scanning
After we have found out that our target is alive, we want to get a more detail picture of the system. The information we need includes:
Open ports and its services
Service versions
Information that the services provided
Operating system
For the port status, we can obtain a total of 6 different results:
| Status | Meaning | |
|---|---|---|
| open | This indicates that the connection to the scanned port has been established. These connections can be TCP connections, UDP datagrams as well as SCTP associations. | |
| closed | When the port is shown as closed, the TCP protocol indicates that the packet we received back contains an RST flag. This scanning method can also be used to determine if our target is alive or not. | |
| filtered | Nmap cannot correctly identify whether the scanned port is open or closed because either no response is returned from the target for the port or we get an error code from the target. | |
| unfiltered | This state of a port only occurs during the TCP-ACK scan and means that the port is accessible, but it cannot be determined whether it is open or closed. | |
| open | filtered | If we do not get a response for a specific port, Nmap will set it to that state. This indicates that a firewall or packet filter may protect the port. |
| closed | filteredThis state only occurs in the IP ID idle scans and indicates that it was impossible to determine if the scanned port is closed or filtered by a firewall. |
Discovering Open TCP Ports
Nmap will automaticlly do default scan if we do not give any parameters.
If we run as root account, Nmap defaultly scan the top 1000 TCP ports with a SYN scan or -sS.
If we run as user account, Nmap defaultly run TCP scan or -sT to the top 1000 ports by default.
We can also define scanning ports:
-p 22,25,80,139,445 scans these ports one by one, but outputs one report
-p 22 25 80 139 445 scans these ports one by one, but outputs several reports
-p 22-445 scan this IP range
--top-ports=10 scan top 10 of most frequent ports from Nmap database
-p- scan all ports
-F scan top 100 ports
┌─[✗]─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 --top-ports=10
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 10:36 NZST
Nmap scan report for 10.129.2.47
Host is up (0.52s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp open ssh
23/tcp closed telnet
25/tcp filtered smtp
80/tcp open http
110/tcp filtered pop3
139/tcp filtered netbios-ssn
443/tcp filtered https
445/tcp filtered microsoft-ds
3389/tcp closed ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in 10.36 secondsIn this example, we can see top 10 ports, and some are closed or filtered. Furthermore, we can trace the packets Nmap sentds, then we will see the the details.
-Pn disable the ICMP echo requests
-n disable DNS resolution
--disable-arp-ping disable ARP ping scan
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -p21 --packet-trace -Pn -n --disable-arp-ping
[sudo] password for chao:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 11:49 NZST
SENT (0.0325s) TCP 10.10.14.145:48726 > 10.129.2.47:21 S ttl=52 id=55444 iplen=44 seq=948661652 win=1024 <mss 1460>
RCVD (0.4135s) TCP 10.129.2.47:21 > 10.10.14.145:48726 RA ttl=63 id=0 iplen=40 seq=0 win=0
Nmap scan report for 10.129.2.47
Host is up (0.38s latency).
PORT STATE SERVICE
21/tcp closed ftpIn this example, we see the the packet we sent from our IP address and port 48726 to the target. Then, we receive a packet contains RA(RST and ACK flags) from the target port 21. Let us analysis this:
Request
SENT (0.0325s) send a packet to the target
TCP use TCP protocol
10.10.14.145:48726 > source port
10.129.2.47:21 target port
S SYN flag of the sent TCP packet
ttl=52 id=55444 iplen=44 seq=948661652 win=1024 <mss 1460> Additional TCP header parameters
Response
RCVD (0.4135s) receive a packet from the target
TCP show the protocol that is being used
10.129.2.47:21 > target IP and port, which will be used to reply
10.10.14.145:48726 our IP and port that be replied to
RA RST and ACK flages of the received TCP packet
ttl=63 id=0 iplen=40 seq=0 win=0 Additional TCP hearder parameters
Connect Scan
-sT uses the TCP three-way handshake to determine if a specific port on a target host is open(reply a SYN-ACK packet) or closed(reply to a RST packet).
This method is also called TCP Connect Scan. The connection scan is more accurate than others due to three way handshake. Moreover, it does not leave unfinished connections or unsent packets on the target host, which makes it less likely to be detected by IDS(intrusion detection systems) or IPS(intrusion protection systems), thus causing a minimal impact to target. However, connection scan is more slower than other types of scans as it requires the scanner to wait for a response from the target, which could takes some time if the target is busy.
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.49 -p22 --packet-trace -Pn -n --reason -sT
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 12:19 NZST
CONN (0.0179s) TCP localhost > 10.129.2.49:22 => Operation now in progress
CONN (0.3599s) TCP localhost > 10.129.2.49:22 => Connected
Nmap scan report for 10.129.2.49
Host is up, received user-set (0.35s latency).
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
Nmap done: 1 IP address (1 host up) scanned in 0.36 secondssudo nmap 10.129.2.49 -p21 --packet-trace -Pn -n --reason -sT
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 12:19 NZST
CONN (0.0270s) TCP localhost > 10.129.2.49:21 => Operation now in progress
CONN (0.4317s) TCP localhost > 10.129.2.49:21 => Connection refused
Nmap scan report for 10.129.2.49
Host is up, received user-set (0.41s latency).
PORT STATE SERVICE REASON
21/tcp closed ftp conn-refused
Nmap done: 1 IP address (1 host up) scanned in 0.43 secondsFiltered Ports
Sometimes, a port is shown as filted, it can be several reasons such as firewall have certain rules set to handle specific connections. As a result, the packet can either be dropped, or rejected. By default, the Nmap will retry to send one packet(--max-rate).
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -p25 --packet-trace -n -Pn --max-retries 0
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 12:50 NZST
SENT (0.0281s) TCP 10.10.14.145:37488 > 10.129.2.47:25 S ttl=50 id=65472 iplen=44 seq=2338537727 win=1024 <mss 1460>
Warning: 10.129.2.47 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.129.2.47
Host is up.
PORT STATE SERVICE
25/tcp filtered smtp
Nmap done: 1 IP address (1 host up) scanned in 1.05 seconds┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -p445 --packet-trace -n -Pn --max-retries 1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 12:52 NZST
SENT (0.0214s) TCP 10.10.14.145:41930 > 10.129.2.47:445 S ttl=39 id=44085 iplen=44 seq=2986459191 win=1024 <mss 1460>
SENT (1.0234s) TCP 10.10.14.145:41932 > 10.129.2.47:445 S ttl=52 id=61368 iplen=44 seq=2986590261 win=1024 <mss 1460>
Nmap scan report for 10.129.2.47
Host is up.
PORT STATE SERVICE
445/tcp filtered microsoft-dsDiscovering Open UDP Ports
Some administrators may forget to filter the UDP ports. We do not receive any acknowledgement packet from UDP as UDP is stateless port. Consequencetly, the timeout is much longer, making the UDP scann(-sU) is much slower than the TCP scan(-sS or -sT).
-sU performs a UDP scan
-F scans top 100 ports
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -F -sU
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 12:59 NZST
Nmap scan report for 10.129.2.47
Host is up (0.44s latency).
Not shown: 93 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
137/udp open netbios-ns
138/udp open|filtered netbios-dgm
445/udp open|filtered microsoft-ds
997/udp open|filtered maitrd
1646/udp open|filtered radacct
1813/udp open|filtered radacctAs UDP generally does not reply to us, we do not receive any response unless the application is configured to do so. Otherwise, we cannot determine if the UDP packet has accived at all or not.
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -p137 -sU -Pn -n --disable-arp-ping --packet-trace --reason
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 13:07 NZST
SENT (0.0878s) UDP 10.10.14.145:51510 > 10.129.2.47:137 ttl=37 id=15186 iplen=78
SENT (0.0881s) UDP 10.10.14.145:51510 > 10.129.2.47:137 ttl=37 id=15186 iplen=78
SENT (0.0884s) UDP 10.10.14.145:51510 > 10.129.2.47:137 ttl=56 id=15186 iplen=78
RCVD (0.4745s) UDP 10.129.2.47:137 > 10.10.14.145:51510 ttl=63 id=10026 iplen=221
Nmap scan report for 10.129.2.47
Host is up, received user-set (0.39s latency).
PORT STATE SERVICE REASON
137/udp open netbios-ns udp-response ttl 63
Nmap done: 1 IP address (1 host up) scanned in 0.49 seconds┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.47 -p138 -sU -Pn -n --disable-arp-ping --packet-trace --reason
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 13:07 NZST
SENT (0.0864s) UDP 10.10.14.145:40642 > 10.129.2.47:138 ttl=42 id=28725 iplen=28
SENT (1.0883s) UDP 10.10.14.145:40644 > 10.129.2.47:138 ttl=47 id=48425 iplen=28
Nmap scan report for 10.129.2.47
Host is up, received user-set.
PORT STATE SERVICE REASON
138/udp open|filtered netbios-dgm no-response
Nmap done: 1 IP address (1 host up) scanned in 2.11 secondsIf we get an ICMP response with error code3(port unreachable), we know that the port is indeed closed.
chaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -sU -Pn -n --disable-arp-ping --packet-trace -p 100 --reason
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-15 16:25 CEST
SENT (0.0445s) UDP 10.10.14.2:63825 > 10.129.2.28:100 ttl=57 id=29925 iplen=28
RCVD (0.1498s) ICMP [10.129.2.28 > 10.10.14.2 Port unreachable (type=3/code=3) ] IP [ttl=64 id=11903 iplen=56 ]
Nmap scan report for 10.129.2.28
Host is up, received user-set (0.11s latency).
PORT STATE SERVICE REASON
100/udp closed unknown port-unreach ttl 64
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 0.15 secondsVersion Scan
Another handy method for scanning port is -sVoption which is used to get additional available information from the open ports like versions, service names, and details about the target.
-sV perform a version scan
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 ProFTPD 1.3.5e
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
110/tcp open pop3 syn-ack ttl 63 Dovecot pop3d
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
993/tcp open ssl/imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 syn-ack ttl 63 Dovecot pop3d
Service Info: Host: NIXFUND; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.32 seconds
More port scanning techniques in Nmap offical documents.
Saving the Results
While we run various scans, we should always save the results. Then, we can use these later to examine the differences between the different scanning methods we have used. Nmap can save the results in 3 different formats.
| Command | Meaning | File extension |
|---|---|---|
| -oN | Normal Output | .nmap |
| -oG | Grepable Output | .gnmap |
| -oX | XML Output | .xml |
| -oA | All three Output | .nmap .gnmap .xml |
┌─[✗]─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.80 -sS --open -p- -oA target
[sudo] password for chao:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 13:49 NZST
Nmap scan report for 10.129.2.80
Host is up (0.36s latency).
Not shown: 64216 closed tcp ports (reset), 1316 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
10001/tcp open scp-config
Nmap done: 1 IP address (1 host up) scanned in 141.09 secondsIf no full path is given, the results will be stored in the directory we are currently in.
┌─[chao@parrot]─[~/Desktop]
└──╼ $ls
Academy Lab README.license target.gnmap target.xml
academy-regular.ovpn lab_chaostudy.ovpn Script target.nmapThree types of results has different format:
Normal Output
┌─[chao@parrot]─[~/Desktop]
└──╼ $cat target.nmap
# Nmap 7.94SVN scan initiated Wed Jul 17 13:49:16 2024 as: nmap -sS --open -p- -oA target 10.129.2.80
Nmap scan report for 10.129.2.80
Host is up (0.36s latency).
Not shown: 64216 closed tcp ports (reset), 1316 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
10001/tcp open scp-config
# Nmap done at Wed Jul 17 13:51:37 2024 -- 1 IP address (1 host up) scanned in 141.09 secondsGrepable Output
┌─[chao@parrot]─[~/Desktop]
└──╼ $cat target.gnmap
# Nmap 7.94SVN scan initiated Wed Jul 17 13:49:16 2024 as: nmap -sS --open -p- -oA target 10.129.2.80
Host: 10.129.2.80 () Status: Up
Host: 10.129.2.80 () Ports: 22/open/tcp//ssh///, 80/open/tcp//http///, 10001/open/tcp//scp-config///
# Nmap done at Wed Jul 17 13:51:37 2024 -- 1 IP address (1 host up) scanned in 141.09 secondsXML Output
┌─[chao@parrot]─[~/Desktop]
└──╼ $cat target.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE nmaprun>
<?xml-stylesheet href="file:///usr/bin/../share/nmap/nmap.xsl" type="text/xsl"?>
<!-- Nmap 7.94SVN scan initiated Wed Jul 17 13:49:16 2024 as: nmap -sS --open -p- -oA target 10.129.2.80 -->
<nmaprun scanner="nmap" args="nmap -sS --open -p- -oA target 10.129.2.80" start="1721180956" startstr="Wed Jul 17 13:49:16 2024" version="7.94SVN" xmloutputversion="1.05">
<scaninfo type="syn" protocol="tcp" numservices="65535" services="1-65535"/>
<verbose level="0"/>
<debugging level="0"/>
<hosthint><status state="up" reason="unknown-response" reason_ttl="0"/>
<address addr="10.129.2.80" addrtype="ipv4"/>
<hostnames>
</hostnames>
</hosthint>
<host starttime="1721180962" endtime="1721181097"><status state="up" reason="echo-reply" reason_ttl="63"/>
<address addr="10.129.2.80" addrtype="ipv4"/>
<hostnames>
</hostnames>
<ports><extraports state="closed" count="64216">
<extrareasons reason="reset" count="64216" proto="tcp" ports="1-21,23-24,996-1488,1490-1846,1848-1958,1960-2321,2323-2563,2565-2675,2677-2800,2802-2861,2863-2865,2867-2875,2877-3123,3125-3139,3141-3374,3376-3422,3424-3534,3536-4063,4065-4227,4229-4516,4518-4663,4665-4910,4912-5709,5711-6327,6329-6436,6438-6496,6498-7032,7034-7273,7275-7342,7344-8015,8017-8050,8052-8091,8093-8807,8809-8914,8916-8966,8968-9001,9003-9016,9018-9398,9400,9402-9616,9618-9809,9811-10000,10002-10111,10113-10286,10288-10534,10536-10547,10549-10700,10702-10775,10777-10800,10802-11268,11270-11350,11352-11614,11616-11715,11717-11982,11984-12145,12147-12305,12307-12397,12399-12414,12416-13223,13225-13453,13455-13682,13684-13706,13708-13865,13867-13969,13971-14268,14270-14351,14353-14387,14389-14437,14439-14555,14557-15161,15163-15426,15428-15898,15900-15951,15953-15967,15969-16163,16165-16508,16510-16566,16568-16616,16618-16764,16766-17021,17023-17141,17143,17145-17146,17148-17516,17518-17609,17611-17653,17655-17861,17863-17916,17918-18171,18173-18214,18216-18351,18353-18394,18396-18754,18756-18811,18813-19318,19320-19519,19521-19595,19597-19661,19663-19739,19741-19745,19747-19829,19831-20024,20026-20409,20411-20908,20910-21247,21249-21308,21310-21434,21436-21839,21841-22097,22099-22376,22378-22551,22553-22702,22704-22761,22763-22796,22798-22851,22853-23136,23138-23162,23164-23283,23285-23557,23559-23589,23591-23615,23617-23838,23840-23902,23904-24095,24097-24139,24141-24405,24407-24476,24478-24530,24532-24854,24856-24948,24950-25098,25100-25361,25363-25494,25496-25552,25554-25734,25736-25855,25857-26097,26099-26125,26127-26165,26167-26224,26226-26470,26472-27163,27165-27353,27355-27979,27981-28114,28116-28260,28262-28289,28291-28327,28329-28589,28591-28728,28730-28843,28845-29240,29242-29345,29347-29414,29416-29451,29453-29856,29858-30025,30027-30052,30054-30171,30173-30245,30247-30413,30415-30452,30454-30663,30665-30975,30977-31097,31099-31148,31150-31184,31186-31622,31624-31920,31922-32199,32201-32440,32442-32459,32461-32500,32502-32533,32535-32663,32665-32666,32668-32803,32805-33114,33116-33208,33210-33272,33274-33527,33529-33576,33578-33716,33718-33956,33958-34055,34057-34198,34200-34375,34377-34478,34480-34514,34516-34580,34582-34648,34650-34832,34834-34988,34990-35161,35163-35410,35412-35715,35717-36109,36111-36235,36237-36244,36246-36720,36722-36747,36749-36797,36799-36952,36954-36986,36988-37347,37349-37472,37474-37475,37477-37528,37530-37577,37580-37642,37644-37932,37934-37973,37975-38196,38198-38365,38367-38641,38643-38731,38733-38853,38855-39011,39013-39038,39040-39108,39110-39250,39252-39340,39342-39521,39523-40070,40072-40089,40091-40202,40204-40339,40341-40552,40554-40662,40664-40865,40867-40932,40934-40958,40960-41007,41009-41383,41385-41688,41690-41969,41971-42132,42134-42136,42138-42167,42169-42304,42306-43471,43473-43518,43520-43550,43552-43670,43672-43709,43711-43755,43757-43976,43978-43982,43984-44043,44045-44208,44210-44408,44410-44534,44536-44753,44755-44943,44945-44985,44987-45403,45405-45429,45431-45684,45686-45855,45857-46075,46077-46232,46234-46397,46399-46546,46548-46563,46565-46887,46889-47065,47067-47347,47349-47380,47382-47559,47561-48262,48264-48552,48554-48565,48567-48740,48742-49084,49086-49132,49134-49356,49358-49376,49378-49801,49803-50367,50369-50390,50392-50419,50421-50551,50553-50567,50569-50721,50723-50841,50843-51188,51190-51382,51384-51452,51454-51610,51612-51746,51748-52099,52101-52151,52153-52380,52382-52438,52440-52712,52714-53061,53063-53175,53177-53748,53750-53789,53791-54185,54187-54401,54403-54702,54704-55671,55673-55844,55846-55900,55902-56207,56209-56698,56700-56714,56716-56836,56838-57008,57010-57726,57728-57831,57833-57861,57863-57934,57936-58088,58090-58533,58535-58683,58685-58734,58736-58912,58914-59047,59049-59539,59541-59600,59602-60759,60761-60809,60811-60984,60986-61634,61636-61705,61707-61956,61958-62285,62287,62289-62686,62688-62790,62792-62900,62902-63136,63138-63231,63233-63284,63286-63297,63299-63382,63384-63555,63557-63751,63753-63966,63968-64227,64229-64234,64236-64616,64618-64909,64911-65152,65154-65215,65217-65351,65353-65535"/>
</extraports>
<extraports state="filtered" count="1316">
<extrareasons reason="no-response" count="1316" proto="tcp" ports="25-79,81-995,1489,1847,1959,2322,2564,2676,2801,2862,2866,2876,3124,3140,3375,3423,3535,4064,4228,4517,4664,4911,5710,6328,6437,6497,7033,7274,7343,8016,8051,8092,8808,8915,8967,9002,9017,9399,9401,9617,9810,10112,10287,10535,10548,10701,10776,10801,11269,11351,11615,11716,11983,12146,12306,12398,12415,13224,13454,13683,13707,13866,13970,14269,14352,14388,14438,14556,15162,15427,15899,15952,15968,16164,16509,16567,16617,16765,17022,17142,17144,17147,17517,17610,17654,17862,17917,18172,18215,18352,18395,18755,18812,19319,19520,19596,19662,19740,19746,19830,20025,20410,20909,21248,21309,21435,21840,22098,22377,22552,22703,22762,22797,22852,23137,23163,23284,23558,23590,23616,23839,23903,24096,24140,24406,24477,24531,24855,24949,25099,25362,25495,25553,25735,25856,26098,26126,26166,26225,26471,27164,27354,27980,28115,28261,28290,28328,28590,28729,28844,29241,29346,29415,29452,29857,30026,30053,30172,30246,30414,30453,30664,30976,31098,31149,31185,31623,31921,32200,32441,32460,32501,32534,32664,32667,32804,33115,33209,33273,33528,33577,33717,33957,34056,34199,34376,34479,34515,34581,34649,34833,34989,35162,35411,35716,36110,36236,36245,36721,36748,36798,36953,36987,37348,37473,37476,37529,37578-37579,37643,37933,37974,38197,38366,38642,38732,38854,39012,39039,39109,39251,39341,39522,40071,40090,40203,40340,40553,40663,40866,40933,40959,41008,41384,41689,41970,42133,42137,42168,42305,43472,43519,43551,43671,43710,43756,43977,43983,44044,44209,44409,44535,44754,44944,44986,45404,45430,45685,45856,46076,46233,46398,46547,46564,46888,47066,47348,47381,47560,48263,48553,48566,48741,49085,49133,49357,49377,49802,50368,50391,50420,50552,50568,50722,50842,51189,51383,51453,51611,51747,52100,52152,52381,52439,52713,53062,53176,53749,53790,54186,54402,54703,55672,55845,55901,56208,56699,56715,56837,57009,57727,57832,57862,57935,58089,58534,58684,58735,58913,59048,59540,59601,60760,60810,60985,61635,61706,61957,62286,62288,62687,62791,62901,63137,63232,63285,63298,63383,63556,63752,63967,64228,64235,64617,64910,65153,65216,65352"/>
</extraports>
<port protocol="tcp" portid="22"><state state="open" reason="syn-ack" reason_ttl="63"/><service name="ssh" method="table" conf="3"/></port>
<port protocol="tcp" portid="80"><state state="open" reason="syn-ack" reason_ttl="63"/><service name="http" method="table" conf="3"/></port>
<port protocol="tcp" portid="10001"><state state="open" reason="syn-ack" reason_ttl="63"/><service name="scp-config" method="table" conf="3"/></port>
</ports>
<times srtt="359771" rttvar="1983" to="367703"/>
</host>
<runstats><finished time="1721181097" timestr="Wed Jul 17 13:51:37 2024" summary="Nmap done at Wed Jul 17 13:51:37 2024; 1 IP address (1 host up) scanned in 141.09 seconds" elapsed="141.09" exit="success"/><hosts up="1" down="0" total="1"/>
</runstats>
</nmaprun>For the XML format, we can easily convert it to HTML format for us to read with a clear and structured presentation.
xsltproc convert file to other format
┌─[chao@parrot]─[~/Desktop]
└──╼ $xsltproc target.xml -o target.html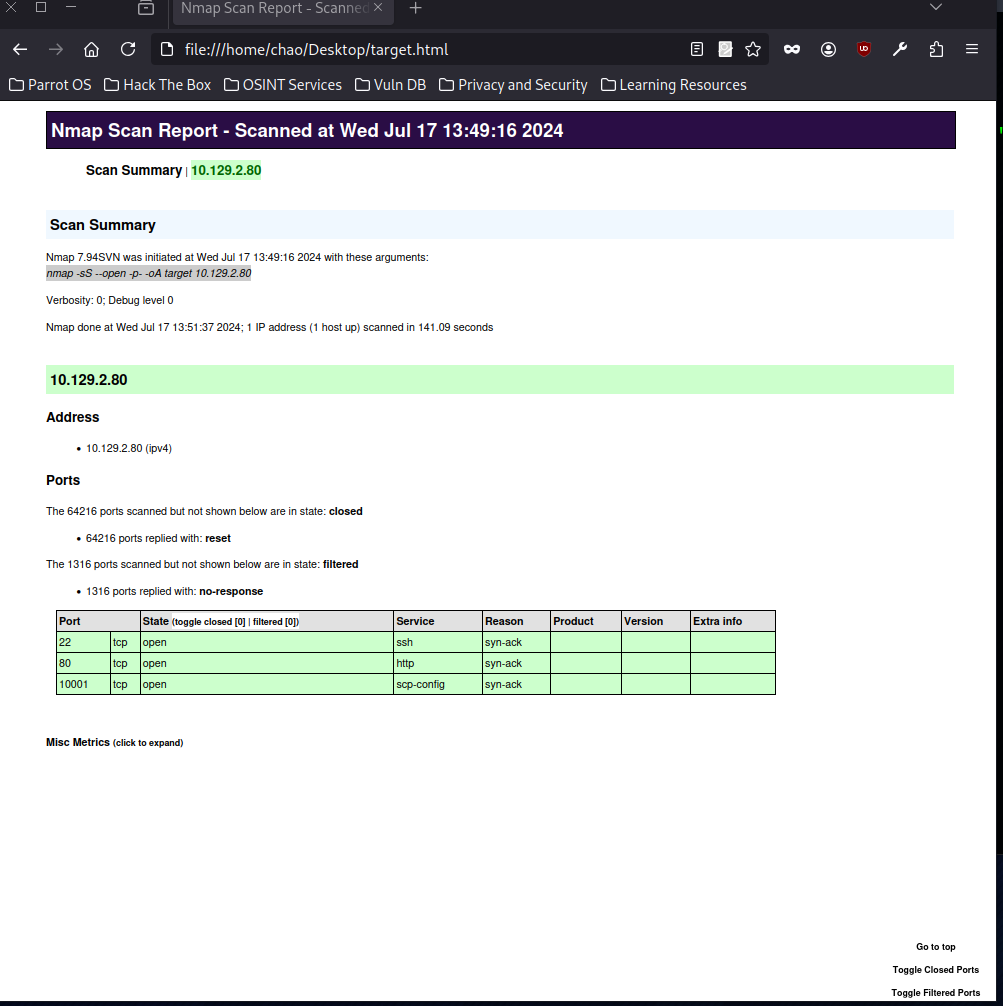
More information can be found in offical document about output formats.
Service Enumeration
It is essential to determine the application and its version as accurately as possible. We can use this information to scan for known vulnerabilities and analyze the source code for that version if we find it.
Service Version Detection
It is recommandation to perform a quick port version scan first, which give us a overoview of the target. Also, it is not easy to be discovered and blocked by the security mechanisms.
-p- all open ports
-sV version scan
space bar allow to view the scan status while the scan when we press this button
┌─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.32 -p- -sV
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 10:51 NZST
Stats: 0:01:33 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 3.32% done; ETC: 11:35 (0:42:45 remaining)--stats-every=5s another option that allow use to define the number of seconds (s) or minutes (m), after which we want to get the status.
┌─[✗]─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.32 -p- -sV --stats-every=5s
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 10:56 NZST
Stats: 0:00:05 elapsed; 0 hosts completed (0 up), 1 undergoing Ping Scan
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Stats: 0:00:10 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 6.49% done; ETC: 10:57 (0:00:58 remaining)
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 6.21% done; ETC: 10:58 (0:02:16 remaining)
Stats: 0:00:20 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 6.31% done; ETC: 10:59 (0:03:28 remaining)
Stats: 0:00:25 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 6.07% done; ETC: 11:01 (0:04:54 remaining)-v/ -vv verbose mode that show us more directly when Nmap detects open ports
┌─[✗]─[chao@parrot]─[~/Desktop]
└──╼ $sudo nmap 10.129.2.32 -p- -sV -v
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 10:58 NZST
NSE: Loaded 46 scripts for scanning.
Initiating Ping Scan at 10:58
Scanning 10.129.2.32 [4 ports]
Completed Ping Scan at 10:58, 0.37s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 10:58
Completed Parallel DNS resolution of 1 host. at 10:58, 5.56s elapsed
Initiating SYN Stealth Scan at 10:58
Scanning 10.129.2.32 [65535 ports]
Discovered open port 3389/tcp on 10.129.2.32
Discovered open port 22/tcp on 10.129.2.32Banner Grabbing
Once the -sV or version scan is complete, we will see all TCP ports with corresponding service and their versions that are active on the system.
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.47 -p- -sV
[sudo] password for chao:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 11:18 NZST
Nmap scan report for 10.129.2.47
Host is up (0.33s latency).
Not shown: 64562 closed tcp ports (reset), 971 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1976.81 secondsHowever, Nmap can miss some information because Nmap does not know how to handle it.
We can useTcpdump and NC to monitor the traffic between two hosts.
For exmaple, in Nmap:
chaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -p- -sV -Pn -n --disable-arp-ping --packet-trace
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-16 20:10 CEST
<SNIP>
NSOCK INFO [0.4200s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [10.129.2.28:25] (35 bytes): 220 inlane ESMTP Postfix (Ubuntu)..
Service scan match (Probe NULL matched with NULL line 3104): 10.129.2.28:25 is smtp. Version: |Postfix smtpd|||
NSOCK INFO [0.4200s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
Nmap scan report for 10.129.2.28
Host is up (0.076s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)
Service Info: Host: inlane
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.47 secondsIn TCPdump:
chaostudy@htb[/htb]$ sudo tcpdump -i eth0 host 10.10.14.2 and 10.129.2.28
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytesIn Nc:
chaostudy@htb[/htb]$ nc -nv 10.129.2.28 25
Connection to 10.129.2.28 port 25 [tcp/*] succeeded!
220 inlane ESMTP Postfix (Ubuntu)Then back to TCPdump to see the Intercepted Traffic:
18:28:07.128564 IP 10.10.14.2.59618 > 10.129.2.28.smtp: Flags [S], seq 1798872233, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 331260178 ecr 0,sackOK,eol], length 0
18:28:07.255151 IP 10.129.2.28.smtp > 10.10.14.2.59618: Flags [S.], seq 1130574379, ack 1798872234, win 65160, options [mss 1460,sackOK,TS val 1800383922 ecr 331260178,nop,wscale 7], length 0
18:28:07.255281 IP 10.10.14.2.59618 > 10.129.2.28.smtp: Flags [.], ack 1, win 2058, options [nop,nop,TS val 331260304 ecr 1800383922], length 0
18:28:07.319306 IP 10.129.2.28.smtp > 10.10.14.2.59618: Flags [P.], seq 1:36, ack 1, win 510, options [nop,nop,TS val 1800383985 ecr 331260304], length 35: SMTP: 220 inlane ESMTP Postfix (Ubuntu)
18:28:07.319426 IP 10.10.14.2.59618 > 10.129.2.28.smtp: Flags [.], ack 36, win 2058, options [nop,nop,TS val 331260368 ecr 1800383985], length 0[!NOTE]
这条命令使用 tcpdump 捕获网络接口上的数据包,具体解释如下:sudo:以超级用户权限运行命令,因为捕获网络流量通常需要更高的权限。
tcpdump:网络数据包捕获工具。
-i eth0:指定要监听的网络接口为 eth0。
host 10.10.14.2 and 10.129.2.28:捕获数据包的过滤条件,表示只捕获源地址或目的地址是 10.10.14.2 和 10.129.2.28 之一的数据包。
简而言之,这条命令会捕获 eth0 网络接口上所有与 10.10.14.2 或 10.129.2.28 之间的流量。具体来说,它会捕获以下情况的数据包:源地址是 10.10.14.2,目的地址是 10.129.2.28。
源地址是 10.129.2.28,目的地址是 10.10.14.2。
Nmap Scripting Engine
Nmap Scripting Engine or NSE is a very important feature of Nmap. It provides the ability to create normal or customed scripts in Lua for interactive with certain services. In total, there are 14 of categories scripts.
| Category | Description |
|---|---|
| auth | Determination of authentication credentials. |
| broadcast | Scripts, which are used for host discovery by broadcasting and the discovered hosts, can be automatically added to the remaining scans. |
| brute | Executes scripts that try to log in to the respective service by brute-forcing with credentials. |
| default | Default scripts executed by using the -sC option. |
| discovery | Evaluation of accessible services. |
| dos | These scripts are used to check services for denial of service vulnerabilities and are used less as it harms the services. |
| exploit | This category of scripts tries to exploit known vulnerabilities for the scanned port. |
| external | Scripts that use external services for further processing. |
| fuzzer | This uses scripts to identify vulnerabilities and unexpected packet handling by sending different fields, which can take much time. |
| intrusive | Intrusive scripts that could negatively affect the target system. |
| malware | Checks if some malware infects the target system. |
| safe | Defensive scripts that do not perform intrusive and destructive access. |
| version | Extension for service detection. |
| vuln | Identification of specific vulnerabilities. |
Default Scripts
chaostudy@htb[/htb]$ sudo nmap <target> -sCSpecific Scripts Category
chaostudy@htb[/htb]$ sudo nmap <target> --script <category>Defined Scripts
chaostudy@htb[/htb]$ sudo nmap <target> --script <script-name>,<script-name>,...Nmap-Specifying Scripts
chaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -p 25 --script banner,smtp-commands
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-16 23:21 CEST
Nmap scan report for 10.129.2.28
Host is up (0.050s latency).
PORT STATE SERVICE
25/tcp open smtp
|_banner: 220 inlane ESMTP Postfix (Ubuntu)
|_smtp-commands: inlane, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8,
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)--script banner,smtp-commands run two scripts: banner and smtp-commands
Nmap - Aggressive Scan
Nmap also gives us the ability to scan our target with the aggressive option or -oA. This scans the target with multiple options as service detection(-sV), OS dectection (-0), traceroute (--traceroute), and with the default NSE scripts (-sC).
-A Performs multiple options scan
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.47 -p 80 -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 16:33 NZST
Nmap scan report for 10.129.2.47
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 294.29 ms 10.10.14.1
2 294.54 ms 10.129.2.47
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.25 secondsVulnerability Assessment
Nmap also can do vulnerability scan from NSE
-sV Performs service version detection on specified ports
--script vuln Performs all related scripts from specified category
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.47 -p 80 -sV --script vuln
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 16:41 NZST
Nmap scan report for 10.129.2.47
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-server-header: Apache/2.4.29 (Ubuntu)
| vulners:
| cpe:/a:apache:http_server:2.4.29:
| F607361B-6369-5DF5-9B29-E90FA29DC565 9.8 https://vulners.com/githubexploit/F607361B-6369-5DF5-9B29-E90FA29DC565 *EXPLOIT*
| EDB-ID:51193 9.8 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT*
...
...
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.10 secondsMore NSE scripts in offical documentation.
Performance
Scanning performance plays a significant role when we are scanning an extensive network or dealing with low network bandwidth.
-T <0-5> to tell Nmap how fast
--min-parallelistm
--max-rtt-timeout to tell Nmap which timouts
--min-rate
--max-retries
Timeouts
When Nmap sends a packet, it takes some time (Round-Trip-Time-RTT) to receive a response from the scanned port. Generally, Nmap default starts with a high timeout (--min-RTT-timeout) of 100ms.
--initial-rtt-timeout 50ms Sets the specified time value as initial RTT timeout.
--max-rtt-timeout 100ms Sets the specified time value as maximum RTT timeout.
See the below example, scanned times are different
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F
[sudo] password for chao:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:26 NZST
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 69.62 seconds┌─[✗]─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F --initial-rtt-timeout 50ms --max-rtt-timeout 100ms
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:28 NZST
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 128.64 secondsMax Retries
The default retry value is 10, so the scanning speed will be increased if we change the retry rate.
grep "/tcp" looking for line contains /tcp
wc -l word calculate -l means lines
--max-retries 0 Sets the number of retries that will be performed during the scan.
See the difference from the below example,
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F | grep "/tcp" | wc -l
29┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F --max-retries 0 | grep "/tcp" | wc -l
35Rates
In the white-box penetration test, we know the network bandwidth. THne we can set the minimum rate (--min-rate
--min-rate 300 Sets the minimum number of packets to be sent per second.
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:42 NZST
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 22.88 seconds┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F --min-rate 300
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:44 NZST
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 10.17 secondsTimeing
Nmap also offers six different timing templates for us to use. The default is normal.
-T 0 / -T paranoid
-T 1 / -T sneaky
-T 2 / -T polite
-T 3 / -T normal
-T 4 / -T aggressive
-T 5 / -T insane
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:48 NZST
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 21.97 seconds┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.0/24 -F -T 5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 17:48 NZST
Warning: 10.129.2.80 giving up on port because retransmission cap hit (2).
Warning: 10.129.2.47 giving up on port because retransmission cap hit (2).
...
...
Nmap done: 256 IP addresses (6 hosts up) scanned in 16.54 secondsMore about scan performance we can find in offical documentation.
Firewall and IDS/IPS Evasion
A firewall is a security measure against unauthorized connection attempts from external networks. Firewall security system can monitor the network traffic of incoming and outgoing data connection and decides how to handle the connection based on the rules that predefined. For exmaple, passed, ignored, or blocked.
Like the firewall, the intrusion detection system or IDS and intrusion prevention system or IPS are also software-based compontents. IDS and IPS scan the network for potential attacks, ayalyze the traffic, and report any detect attacks or prevent the connection attemps.
Sometimes, we can see the status of ports are shown as filtered, it could be several reasons because of the IDS, IPS, or firewall rules.
The error code could be;
Net Unreachable
Net Prohibited
Host Unreachable
Host Prohibited
Port Unreachable
Proto Unreachable
The packets can either be dropped, or rejected. That is why -sS(TCP SYN Scan) and -sT(Connect Scan) are much easier to filter for IDS/IPS, and firewall than -sA(TCP ACK Scan) as -sA does not need ACK flag.
┌─[✗]─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.48 -p 21,22,53,445 -sS -Pn -n --disable-arp-ping --packet-trace
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 19:20 NZST
SENT (0.0474s) TCP 10.10.14.43:59642 > 10.129.2.48:53 S ttl=54 id=21741 iplen=44 seq=4216766005 win=1024 <mss 1460>
SENT (0.0482s) TCP 10.10.14.43:59642 > 10.129.2.48:21 S ttl=37 id=59686 iplen=44 seq=4216766005 win=1024 <mss 1460>
SENT (0.0489s) TCP 10.10.14.43:59642 > 10.129.2.48:445 S ttl=38 id=14516 iplen=44 seq=4216766005 win=1024 <mss 1460>
SENT (0.0496s) TCP 10.10.14.43:59642 > 10.129.2.48:22 S ttl=38 id=54130 iplen=44 seq=4216766005 win=1024 <mss 1460>
RCVD (0.3472s) TCP 10.129.2.48:21 > 10.10.14.43:59642 SA ttl=63 id=0 iplen=44 seq=1934813721 win=64240 <mss 1340>
RCVD (0.3477s) TCP 10.129.2.48:22 > 10.10.14.43:59642 SA ttl=63 id=0 iplen=44 seq=3005299837 win=64240 <mss 1340>
SENT (2.2492s) TCP 10.10.14.43:59644 > 10.129.2.48:445 S ttl=39 id=21922 iplen=44 seq=4216634935 win=1024 <mss 1460>
SENT (2.2494s) TCP 10.10.14.43:59644 > 10.129.2.48:53 S ttl=42 id=6688 iplen=44 seq=4216634935 win=1024 <mss 1460>
Nmap scan report for 10.129.2.48
Host is up (0.30s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp filtered domain
445/tcp filtered microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 3.48 seconds┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.48 -p 21,22,53,445 -sA -Pn -n --disable-arp-ping --packet-trace
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 19:22 NZST
SENT (0.0441s) TCP 10.10.14.43:50164 > 10.129.2.48:445 A ttl=37 id=65265 iplen=40 seq=0 win=1024
SENT (0.0455s) TCP 10.10.14.43:50164 > 10.129.2.48:21 A ttl=39 id=41915 iplen=40 seq=0 win=1024
SENT (0.0457s) TCP 10.10.14.43:50164 > 10.129.2.48:53 A ttl=49 id=50198 iplen=40 seq=0 win=1024
SENT (0.0458s) TCP 10.10.14.43:50164 > 10.129.2.48:22 A ttl=52 id=23730 iplen=40 seq=0 win=1024
RCVD (0.3426s) TCP 10.129.2.48:21 > 10.10.14.43:50164 R ttl=63 id=0 iplen=40 seq=605670883 win=0
RCVD (0.3427s) TCP 10.129.2.48:22 > 10.10.14.43:50164 R ttl=63 id=0 iplen=40 seq=605670883 win=0
SENT (2.2360s) TCP 10.10.14.43:50166 > 10.129.2.48:53 A ttl=44 id=2280 iplen=40 seq=0 win=1024
SENT (2.2361s) TCP 10.10.14.43:50166 > 10.129.2.48:445 A ttl=42 id=6918 iplen=40 seq=0 win=1024
Nmap scan report for 10.129.2.48
Host is up (0.30s latency).
PORT STATE SERVICE
21/tcp unfiltered ftp
22/tcp unfiltered ssh
53/tcp filtered domain
445/tcp filtered microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 3.46 seconds[!NOTE]
Pay attention that we receive SYN-ACK (SA) flags in -sS, but get RST flag (R) in -sA
1. -sS(SYN 扫描)
描述: 这是 nmap 中默认且最常用的扫描类型之一,也被称为“半开”扫描或“隐形”扫描。
工作原理: 发送一个 SYN 包(用来初始化一个 TCP 连接),并等待目标主机的响应。
如果目标端口开放,它会返回一个 SYN-ACK 包,然后 nmap 发送一个 RST 包以终止连接(不完成三次握手)。
如果端口关闭,它会返回一个 RST 包。
优点: 速度快,对系统影响较小,通常不会被记录在系统日志中,因为连接没有完全建立。
缺点: 需要 root 或超级用户权限。
2. -sT(TCP 连接扫描)
描述: 这是最基本的 TCP 连接扫描类型。
工作原理: 尝试与目标端口建立一个完整的 TCP 连接(完成三次握手)。
如果端口开放,连接将成功建立并立即关闭。
如果端口关闭,连接将被拒绝。
优点: 不需要特殊权限(可以由普通用户执行)。
缺点: 较慢,容易被检测和记录,因为完整的连接尝试会出现在日志中。
3. -sA(ACK 扫描)
描述: 主要用于检测防火墙规则集。
工作原理: 发送一个带有 ACK 标志的 TCP 包,不期待建立连接。
如果收到 RST 包,则表明端口是可达的(可能开放或关闭)。
如果没有响应或收到 ICMP 不可达消息,则表明端口被过滤(防火墙阻止)。
优点: 用于探测防火墙规则和确认防火墙是否存在。
缺点: 不能确定端口是否开放或关闭,只能确定是否被过滤。
总结
-sS: 快速、隐蔽、需要高级权限。
-sT: 完整连接、慢、容易被检测、不需要高级权限。
-sA: 探测防火墙规则,不能确定端口状态。Detect IDS/IPS
IDS and IPS are more difficlut to detect as these are passive traffice monitoring systems. IDS system examine all connections and notify the administrator, then administrator will take appropriate action. While IPS system will not only examine the traffice but also do some actions that configured by administrator to prevent potential attacks.
Once administrator detects a potential attacks, the first step is to block this IP address or these IP addresses. As a result, we will no longer be able to continue our testing.
One good method is using VPS or Virtual private server. If at any time this host is blocked and has no access to the target network, we know administrator must have taken some security measures. Accordingly, we can continue with another VPS.
Decoys
For the above reason, the Decoy scanning methor or -D is the right choice. In this method, Nmap will generate various random (RND) a specific number of IP addresses (for exmaple: 5) separated by a colon (:).
-D RND:5 Generates five random IP addresses that indicates the source IP the connection comes from.
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.47 -p 80 -sS -Pn -n --disable-arp-ping --packet-trace -D RND:5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 19:40 NZST
SENT (0.0494s) TCP 10.10.14.43:44908 > 10.129.2.47:80 S ttl=47 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
SENT (0.0495s) TCP 192.197.133.246:44908 > 10.129.2.47:80 S ttl=38 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
SENT (0.0495s) TCP 82.131.56.11:44908 > 10.129.2.47:80 S ttl=37 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
SENT (0.0495s) TCP 153.2.124.2:44908 > 10.129.2.47:80 S ttl=44 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
SENT (0.0495s) TCP 37.47.177.133:44908 > 10.129.2.47:80 S ttl=46 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
SENT (0.0495s) TCP 170.235.96.58:44908 > 10.129.2.47:80 S ttl=48 id=57260 iplen=44 seq=65289555 win=1024 <mss 1460>
RCVD (0.3414s) TCP 10.129.2.47:80 > 10.10.14.43:44908 SA ttl=63 id=0 iplen=44 seq=632493932 win=64240 <mss 1340>
Nmap scan report for 10.129.2.47
Host is up (0.29s latency).
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 0.36 secondsThe spoofed IP address may be filtered by our ISP or routers. Therefore, we can also specify our VPS servers' IP addresses. Just give -D some address
-D 192.168.1.100,192.168.1.101,192.168.1.102 customed spoofed IP addresses
┌─[chao@parrot]─[~]
└──╼ $sudo nmap 10.129.2.28 -p 80 -sS -Pn -n --disable-arp-ping --packet-trace -D 192.168.1.100,192.168.1.101,192.168.1.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 19:42 NZST
SENT (0.0916s) TCP 192.168.1.100:57288 > 10.129.2.28:80 S ttl=51 id=52528 iplen=44 seq=3394946005 win=1024 <mss 1460>
SENT (0.0916s) TCP 10.10.14.43:57288 > 10.129.2.28:80 S ttl=50 id=52528 iplen=44 seq=3394946005 win=1024 <mss 1460>
SENT (0.0917s) TCP 192.168.1.101:57288 > 10.129.2.28:80 S ttl=42 id=52528 iplen=44 seq=3394946005 win=1024 <mss 1460>
SENT (0.0917s) TCP 192.168.1.102:57288 > 10.129.2.28:80 S ttl=51 id=52528 iplen=44 seq=3394946005 win=1024 <mss 1460>
SENT (1.0924s) TCP 192.168.1.100:57290 > 10.129.2.28:80 S ttl=46 id=1688 iplen=44 seq=3394814935 win=1024 <mss 1460>
SENT (1.0925s) TCP 10.10.14.43:57290 > 10.129.2.28:80 S ttl=47 id=1688 iplen=44 seq=3394814935 win=1024 <mss 1460>
SENT (1.0925s) TCP 192.168.1.101:57290 > 10.129.2.28:80 S ttl=56 id=1688 iplen=44 seq=3394814935 win=1024 <mss 1460>
SENT (1.0925s) TCP 192.168.1.102:57290 > 10.129.2.28:80 S ttl=43 id=1688 iplen=44 seq=3394814935 win=1024 <mss 1460>
Nmap scan report for 10.129.2.28
Host is up.
PORT STATE SERVICE
80/tcp filtered http
Nmap done: 1 IP address (1 host up) scanned in 2.11 secondsWe also can manually specify the source IP address (-S) to test, and this address must be alive.
10.129.2.28 Scans the specified target.
-n Disables DNS resolution.
-Pn Disables ICMP Echo requests.
-p 445 Scans only the specified ports.
-O Performs operation system detection scan.
-S Scans the target by using different source IP address.
10.129.2.200 Specifies the source IP address.
-e tun0 Sends all requests through the specified interface.
chaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -n -Pn -p445 -O
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 01:23 CEST
Nmap scan report for 10.129.2.28
Host is up (0.032s latency).
PORT STATE SERVICE
445/tcp filtered microsoft-ds
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.14 secondschaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -n -Pn -p 445 -O -S 10.129.2.200 -e tun0
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 01:16 CEST
Nmap scan report for 10.129.2.28
Host is up (0.010s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.32 (96%), Linux 3.2 - 4.9 (96%), Linux 2.6.32 - 3.10 (96%), Linux 3.4 - 3.10 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Synology DiskStation Manager 5.2-5644 (94%), Linux 2.6.32 - 2.6.35 (94%), Linux 2.6.32 - 3.5 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4.11 secondsDNS Proxying
Nmap allows us to specify the DNS server (--dns-server
In the next example, we use TCP port 53 as source port that the administrator uses the firewall to control this port and does not filter IDS/IPS, our packets will be trusted and passed through.
chaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -p50000 -sS -Pn -n --disable-arp-ping --packet-trace
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-21 22:50 CEST
SENT (0.0417s) TCP 10.10.14.2:33436 > 10.129.2.28:50000 S ttl=41 id=21939 iplen=44 seq=736533153 win=1024 <mss 1460>
SENT (1.0481s) TCP 10.10.14.2:33437 > 10.129.2.28:50000 S ttl=46 id=6446 iplen=44 seq=736598688 win=1024 <mss 1460>
Nmap scan report for 10.129.2.28
Host is up.
PORT STATE SERVICE
50000/tcp filtered ibm-db2
Nmap done: 1 IP address (1 host up) scanned in 2.06 secondschaostudy@htb[/htb]$ sudo nmap 10.129.2.28 -p50000 -sS -Pn -n --disable-arp-ping --packet-trace --source-port 53
SENT (0.0482s) TCP 10.10.14.2:53 > 10.129.2.28:50000 S ttl=58 id=27470 iplen=44 seq=4003923435 win=1024 <mss 1460>
RCVD (0.0608s) TCP 10.129.2.28:50000 > 10.10.14.2:53 SA ttl=64 id=0 iplen=44 seq=540635485 win=64240 <mss 1460>
Nmap scan report for 10.129.2.28
Host is up (0.013s latency).
PORT STATE SERVICE
50000/tcp open ibm-db2
MAC Address: DE:AD:00:00:BE:EF (Intel Corporate)
Nmap done: 1 IP address (1 host up) scanned in 0.08 seconds--source-port 53 Performs the scans from specified source port.
Similarly, in netcat
chaostudy@htb[/htb]$ ncat -nv --source-port 53 10.129.2.28 50000
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Connected to 10.129.2.28:50000.
220 ProFTPd