Security
Authentication
Symbols, letters, uppercase, lowercase, like $T&gi90^ft!@%,akLP^+ is much more secure than 'thequickbrownfoxjump’.
Complex password is hard to remember, so most of users choose to use the same password for multiple sites. Then, there is a risk when one password is breakdown.
Or, user writes the password down, another risk appear.
Or, user forget and have to select 'forgotten password' frequently, here is another risk....
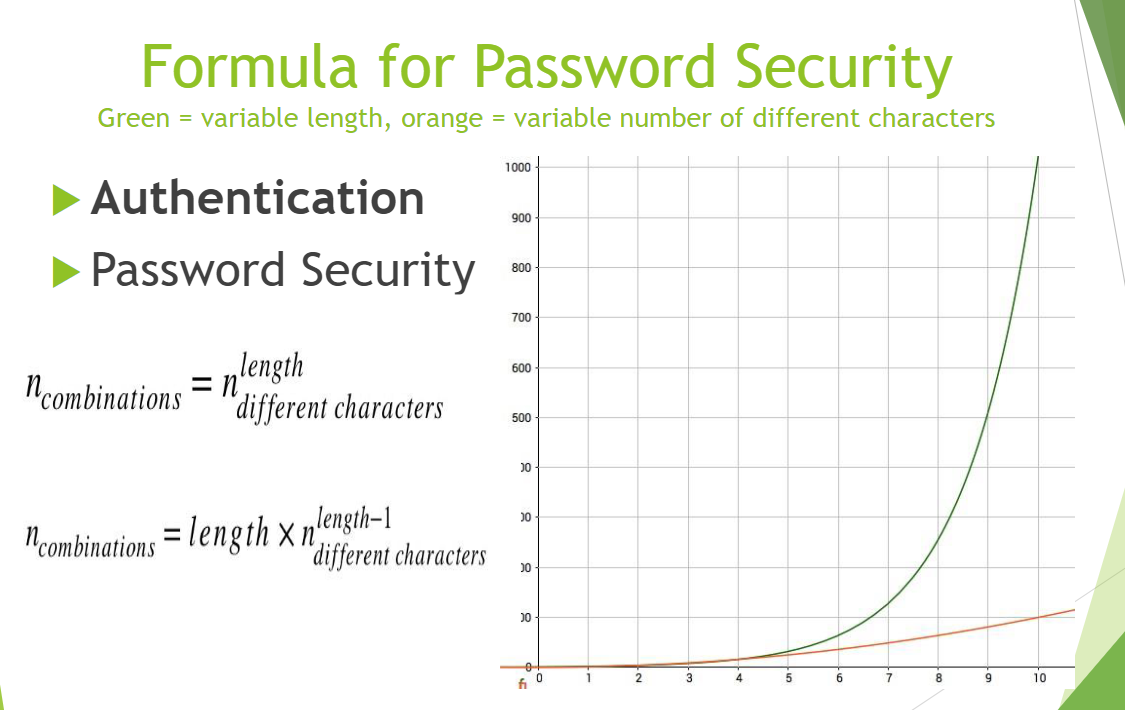
According to this diagram, we know the length of the password is more important, and then variable characters has much less effect on the security of the password.
Password length makes a big difference and can compensate for simple password.
| Variable | Length |
|---|---|
| Lowercase | 26^ 4 = 456 976 |
| Lower, upper, numbers | 62 ^ 4 = 14 776 336 |
| Lowercase | 26 ^ 5 = 11 881 376 |
| Lower, upper, numbers | 62 ^ 5 = 916 132 832 |
| Lowercase | 26 ^ 6 = 3 089 157 766 |
| Lowercase | 26 ^ 7 = 8 031 810 176 |
Iphone pin number only have 4 numbers which is 10000 possible, but iphone use Enclave Processor and several attempts then locked out, and cloud locker.
Some phones use pattern, but actually it is even less secure than a pin
| PIN | Pattern |
|---|---|
| 4 = 10 000 | 1624 |
| 5 = 100 000 | 7152 |
| 6 = 1000 000 | 26016 |
Total pattern possible is 389112 patterns.
The more secure way is 2FA (two factor authentication) or MFA (Multiple factor authentication)
Factors are: what you know, what you have, and who you are
So, it is like that password + fingerprint, tested code or RFID
Authentication Cards:
-
Proximity cards(not swipe cards). It use DESFire tech which require more energe, more time so more security. 3DES cryptographic.
-
Mifare cards. 125Khz is one-way communication. Transmits when powered up. 13.56MHz which originally for transport systems. More secure conversation, so more time required. Encrypts data transferred between the card and the reader. Use AES256 algorithm. Mifare CSN(Card Serial Number) is not encrypted and can be read by cell phones.
Authorisation
Authorisation defines what someone is allowed to do: Read, Write, Modify, and Delete.
Authorised to device or person
Confidentiality
Keep our messages confidential between sender and receiver, the authentication and authorisation do some work but not always useful. For instance, how about wireless communications which is broadcast.
So, we need cryptography, you can read message, but you cannot understand it.
Integrity
Keep the message received is the same as the message sent.
So, we need Hash values, CRC (Cyclic Redundancy Checksum).
Availability
Keep the infrastructure alive and work. Many threatens like power issues, software failure, Dos, Bot, etc.
Non-Repudiation
cannot conduct business over the internet if we cannot make contracts
So, we need digital signatures, laws, etc.
In an ideal world
Security is a constant battle, technology is constantly changing, and the bad guys are always one step ahead.
Forensics
Log Files
Log files may contain useful information:
What has happened?
How it happen?
Is there a vulnerability?
Internal or External?
What do need to do?
We begin the investigation process by securing the evidence so that id does not change.
Challenge:
It is impossible to interrupt the network when we seize the computer, switcher, router.
Log files can be switched off or on,
Different operating systems locate log files in different place.
Log files can be altered by an attacker
Software
Event Viewer
In the early version of Windows, the size of logs was 20MB, but now any size can be reserved.
FAT32=4.3GB (232) exFAT 16 exabytes PB NTFS= 16 exabytes (264)
Calculate size: In an organisation we have 5000 events per day. Each log is approx. 500 bytes. We want to keep 12 months of logs.
5000 x 500 bytes = 2500MB per day x 365 = 912,400 MB (1TB approx)
Network Logs
Most of devices have logs, we must understand the functionality to understand what does not look "right".
For instance, firewall logs, we need look at inbound connection requests, suspicious IP connection attempts, port requests, tracert, whois query
Lab
Lab contains Autopsy, HstEx and NetAnalysis.
